BLOCKCHAIN SECURITY
June 1, 2022 2022-10-05 8:36BLOCKCHAIN SECURITY
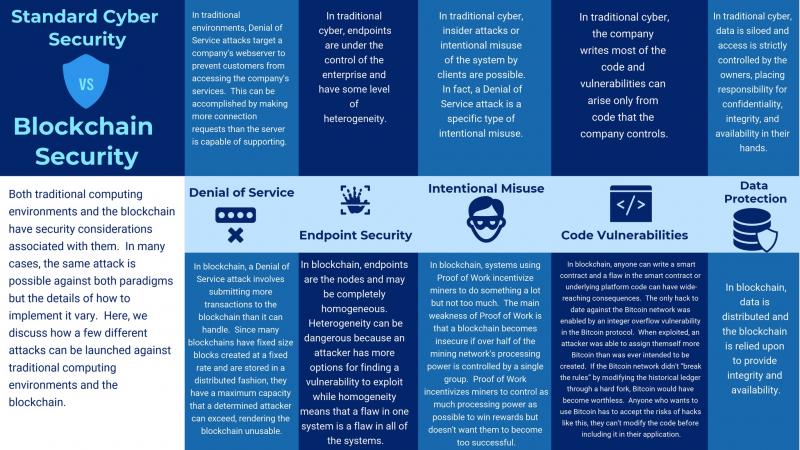
Every technology has its own challenges in terms of achieving maximum security.

BKTRON consultancy areas will include the below but are not limited to :
1. Selection of programming languages, frameworks, etc. in a way to avoid ‘Using Components with Known Vulnerabilities’
2. Creation of business requirement document to envision functionality, security requirements, blockchain permissions, consensus permissions, etc. This is to ensure secure business requirement review and secure network architecture review takes place over a period of time and all changes are tracked, version and approved.
blockchain permissions and consensus mechanisms
3. Appropriate change, incident and patch management process with defined SLA’s
4. Secure Configuration Review documents for all frameworks, softwares, server flavors, etc. used in making of the blockchain product – this is to ensure all the components have optimum secure configuration during the initial stage itself.
5. Secure Code Review during each stage to build the code securely over a period of time and come up with the secure build(the build may be firmware or an application, etc.)
6. Vulnerability Assessment, Penetration Testing, API Testing, Application Testing(Web/Mobile) of the servers, hardware wallets, app/dapp testing, etc.
7. Smart contracts assessments/testing/permission review, firmware testing, load testing, hardware testing, etc. depending on the blockchain product/solution
8. Firewall review – review of all firewall rules for each component/nodes
9. Database review – review of roles, data storage mechanisms, etc.
10. Data Review – Review of data during each stage of the product life cycle to ensure sensitive data is well managed and compliance from data security laws perspective levels like GDPR are achieved
11. Audit and Log Management Review – To ensure that all aspects of the logging and error management are done securely and only non-sensitive logs/events/error messages are accessible to the end user
12. Forensic Readiness Review – To ensure that the product has all possible forensic level readiness to be able to perform forensic review asap in case of an attack